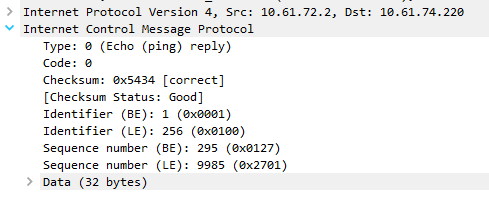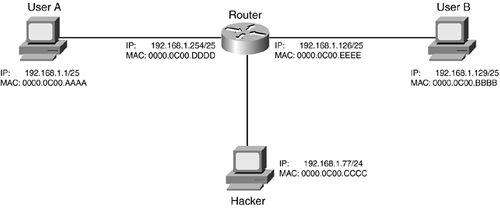
Disabling Interface Services :: Chapter 4. Disabling Unnecessary Services :: Part II: Managing Access to Routers :: Router firewall security :: Networking :: eTutorials.org
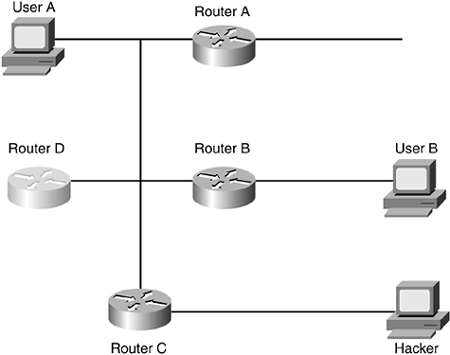
Disabling Interface Services :: Chapter 4. Disabling Unnecessary Services :: Part II: Managing Access to Routers :: Router firewall security :: Networking :: eTutorials.org
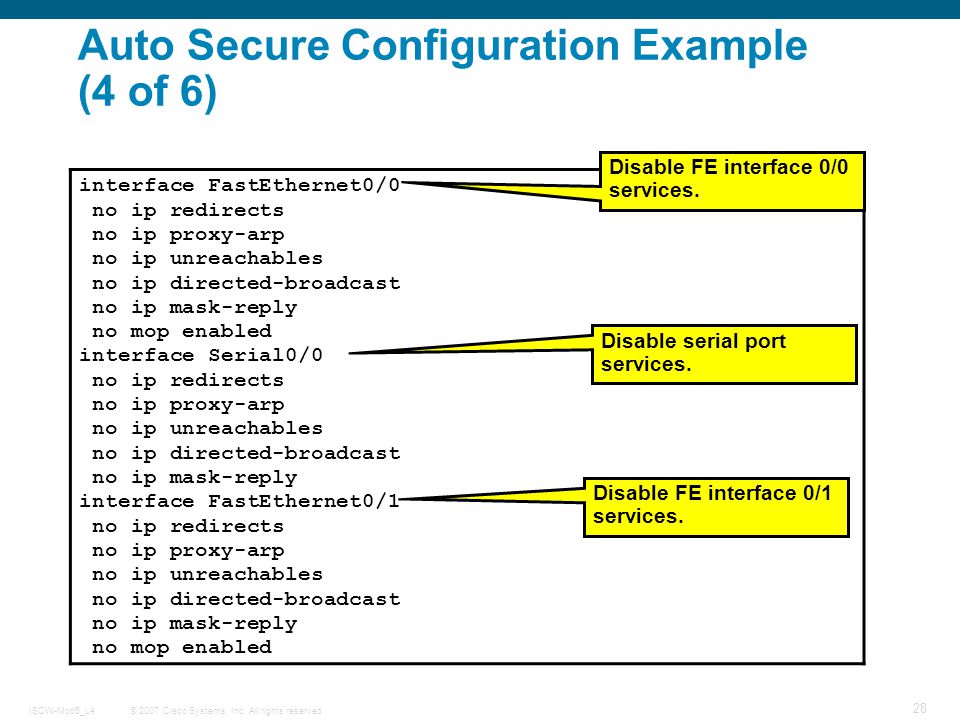
2007 Cisco Systems, Inc. All rights reserved.ISCW-Mod5_L4 1 Implementing Secure Converged Wide Area Networks (ISCW) - ppt download
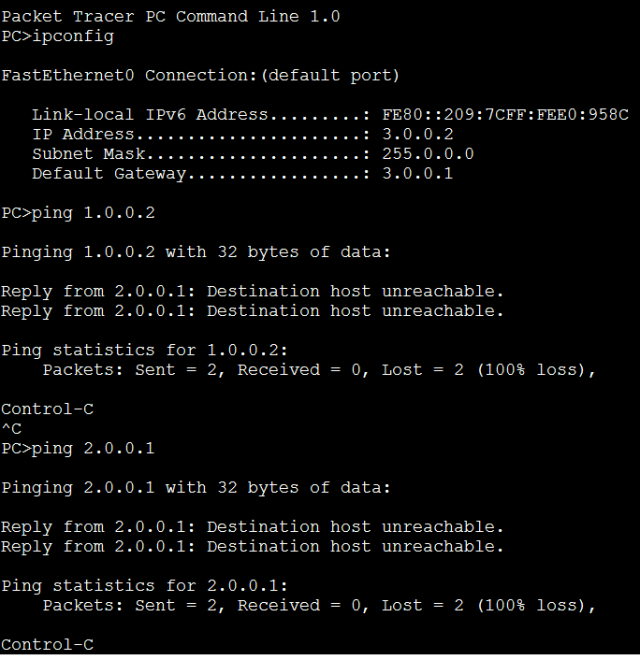
Block icmp or ping using extended acl : a cisco packet tracer lab | Learn Linux CCNA CEH IPv6 Cyber-Security Online



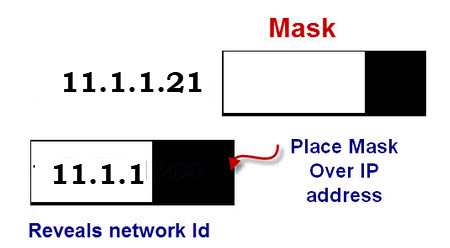


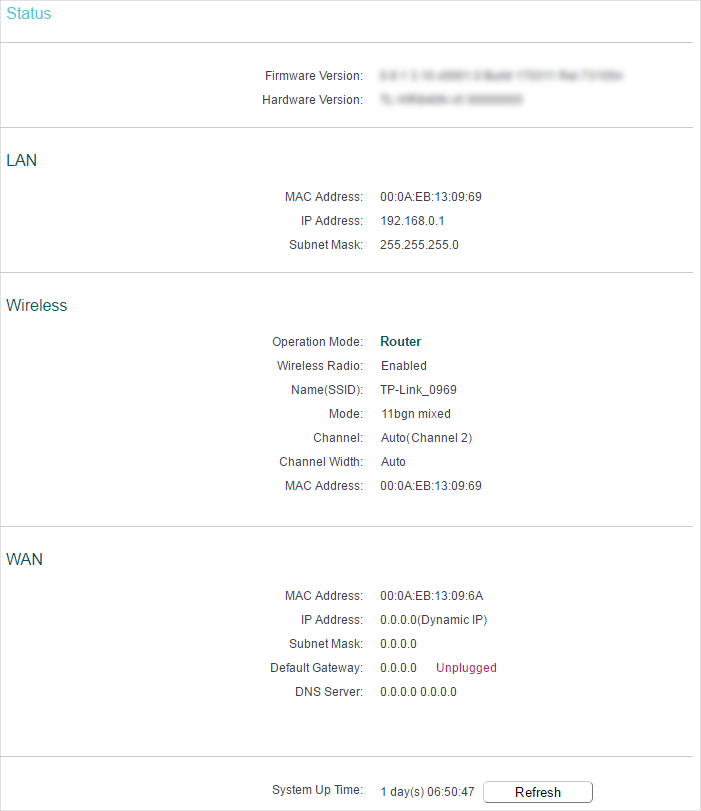

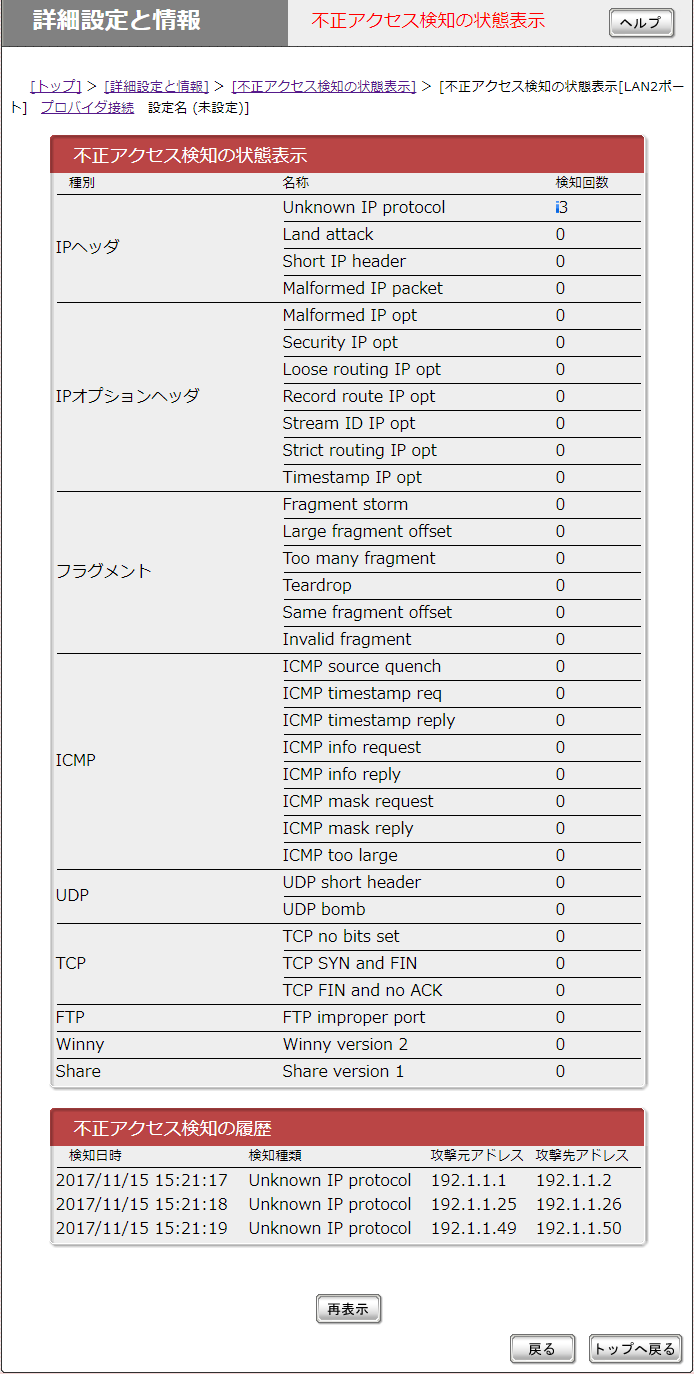





![네트워크장비/기능관리] mask-reply 차단 (N-37) 네트워크장비/기능관리] mask-reply 차단 (N-37)](https://blog.kakaocdn.net/dn/dj8JH2/btriaQspd5D/pfYpUEHLMTf4vCrEo79BRK/img.png)